Let’s Do This Together.
Designing and implementing security training programs can be time-consuming and difficult – we know. You may have lots of roles to train, be unsure of which courses to assign, or struggle with measurement. An experienced Customer Success Manager (CSM) is your trusted adviser to drive completion rates, increase voluntary learning, and achieve objectives.
Customer Success Stories
Led by our Customer Success Team, see how these organizations use our training solutions to mature staff competency.

RELX Group, a $10B publishing company, was rapidly moving from a traditional print information provider to a leader in web-based, digital solutions. Keenly aware that their organizational attack surface had significantly expanded, they sought to protect new digital platforms from the outset.
RELX wanted a training partner who could help them build the security skills needed to match the agility of their new platforms. Security Innovation tailored a program specific to RELX’s tech stack and job functions with a tiered “belt” system that increased in difficulty as learners progressed. This deliberate approach was designed to mitigate new threats in emerging technologies so they could build features with multiple layers of protection more rapidly. It also resulted in the following:
- Less time spent patching retroactive security discoveries
- Ability to measure expectations for each developer
- Mandatory on-boarding security training for all new hires
- Standardized ways to classify capabilities and security training requirements by job function
“Security concerns can’t take a back seat to functionality, so making
developers security-savvy requires a contextual and measured approach.”–Alex Fry, Vice President of Software Security Assurance
 The CISO of Orvis, the oldest mail-order retailer in the United States, wanted to replicate the training success he had as CISO at a different Fortune 500 company. To meet their annual PCI DSS security training requirements, they historically relied on mandatory video training followed by tests to demonstrate completion. While this achieved compliance, it didn’t engage teams in a way that changed behavior.
The CISO of Orvis, the oldest mail-order retailer in the United States, wanted to replicate the training success he had as CISO at a different Fortune 500 company. To meet their annual PCI DSS security training requirements, they historically relied on mandatory video training followed by tests to demonstrate completion. While this achieved compliance, it didn’t engage teams in a way that changed behavior.
The team wanted to take a fresh approach and decided to run a “capture the flag” (CTF) tournament using the CMD+CTRL cyber range. While they hoped for enthusiastic participation, they never expected such wildly successful results:
- Generated Excitement & Passion – teams were so engaged that they no longer dreaded annual training. Training went from being met with sighs to teams asking for multiple sessions. They were literally begging to be part of the training program.
- Created Apprenticeship program – while this was not planned, Security Champions emerged organically. Several developers continued their pursuit of security principles beyond the events, so much so that they were able to lead future events and provide on-the-job mentorship.
- Increased Collaboration – players shared techniques and solutions with each other. Junior developers learned from senior members. This was impossible with the previous individual training.
“We began with a single cyber range event. It generated so much excitement
that teams immediately asked when we are running the next one”–Joe Mineri, CISO
This company builds and manages software systems for the world’s most recognizable brands. As such, they have clauses that hold them accountable to demonstrate security competency for their teams. In early 2019, they sought to train nearly 80,000 employees. They realized this would be challenging as they had staff in 12 different countries and over 50 job functions of varying maturity levels.
Guided by a Security Innovation Customer Success Manager, we devised a plan with:
- Learning paths for 24 roles based on 3 skill levels, each with clear objectives
- Computer-based Training (CBT) coupled with a “practice area” using CMD+CTRL Cyber Range
- Pilot programs to ensure seamless rollout for larger audiences
- Post-training assessments to determine if users should advance to the next level
- Communication plans complete with emails, social media posts, and scheduled prompts
Security Innovation ran four cyber range events throughout the year, targeting a full range of software engineering skill levels. Over 500 participated, both online and on-site, resulting in more than 100 job placements into other business units and the creation of dozens of new security champions.
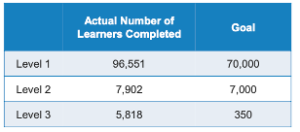
At the end of 2019, all goals were exceeded:
a total of 1,118,382 course hours were consumed
in twelve months
One of the most influential software companies over the past 30 years had several needs:
- Train thousands of software architects, developers, tester, & product managers on The Microsoft Security Development Lifecycle (SDL)
- Use hands-on exercises in a competitive but fun way to assess competency and build awareness for software development and deployment teams around the globe.
- Help staff and customers better understand Azure configuration and deployment security
Security Innovation developed 14 computer-based courses on different SDL topics from threat modeling to secure coding and security test execution. These have been since updated thrice and modularized into micro-learning modules. The company was able to measure a significant reduction in security vulnerabilities pre- and post-training for two of its flagship product lines and made the findings public.
The company currently uses CMD+CTRL Cyber Range to run competitive and awareness events to increase security expertise:
- Durations range from one to thirty days, each targeting 200 – 1,000 people. Support is provided via the Chat channel that is monitored by Security Innovation experts. The first two events had no CBT component. After introducing How to Test for OWASP Top Ten CBT, scores increased an average of 25%. This training is now part of player on-boarding.
- Hands-on practice field for secure Azure deployment: leveraging an Azure cyber range Security Innovation built for them, they run bi-weekly events for staff and plan to run them for their top clients to help them better understand Azure-specific configuration vulnerabilities.
After a few engineers participated in a Security Innovation open enrollment Cyber Range event, this led to an interest in a broader internal event at company headquarters. The company ran a one-day pilot event that was supported by a Security Innovation instructor. Based on high engagement and player feedback, they decided to run quarterly events where different ranges would increase in difficulty and be used for varying roles:
- Shadow Bank – banking website with a mix of easy and intermediate challenges: cross-site scripting, password cracking, authorization bypass, business logic abuse, and others
- Gold Standard: advanced banking website that builds upon the challenges in Shadow Bank and includes poorly implemented defenses making them more difficult
- Shadow Bank: repeated in 3rd event targeting a different set of software security stakeholders
- Shred Skateboards: e-commerce system with different challenges like weak cryptography, parameter tampering, and others
High-scoring players were awarded prizes and notable results such as first-time participants or most improved scores were highlighted in the company newsletter.
“Well organized, good mix of easy and hard exploits”
“If I can see how attackers penetrate my applications, I can better prepare them”
FinCo wanted to improve application security skills in DevOps and IT teams via coursework and hands-on activities. Computer-based training (CBT) was used to build foundational knowledge and the cyber range to apply it in practice. Other program elements included:
- Customized Training Portal: ability to customize branding, billboards, DevOps-specific messages
- Job-specific Learning Paths: we created 21 role- and technology-based learning paths in 3 progressive tiers: fundamental, intermediate, and advanced.
- Competitive hands-on events: time-boxed, tournament-style competitions using CMD+CTRL cyber range. To qualify, employees had to complete at least one fundamental learning path.
Given the global distribution of the workforce, competitions were managed as follows:
- Sent 5,000 invitations per month, resulting in ~1,000 participants per months
- 3-weeks of 24×7 access to the Cyber Range (averaged 8-10 hours/player)
- Regular cadence of emails: reminders to register, encouragement to the bottom 20%, extra hints, top scores, and pre-recorded learning labs
Cyber range reports identified gaps and led to learning path adjustments. Additionally, there was a noticeable improvement in the team’s awareness of vulnerabilities and interest in actually fixing them.
In the absence of mandatory training, the CBT pre-requisite to compete in the cyber range event increased consumption by 30%