SecureOps BLENDED TRAINING
Ensure IT & Operations Teams
can Hold the Security Line
With security activities increasingly being pushed on to them, IT teams need a partner who can arm them with ongoing expertise and cutting-edge learning methods.
SecureOps combines on-demand courses with hands-on cyber ranges to build the skills needed to:
|
|
Build Skills in a Familiar Environment
SecureOps features role-based learning paths tiered to the desired competency. Courses quickly scale knowledge and cloud-based cyber ranges provide an immersive way to uncover poorly implemented principles in real IT systems.
 |
 |
|
|
Traditional training is necessary but not sufficient to meet the demand of qualified workers.
A key tool for reducing the skills gap is the cyber range - NIST
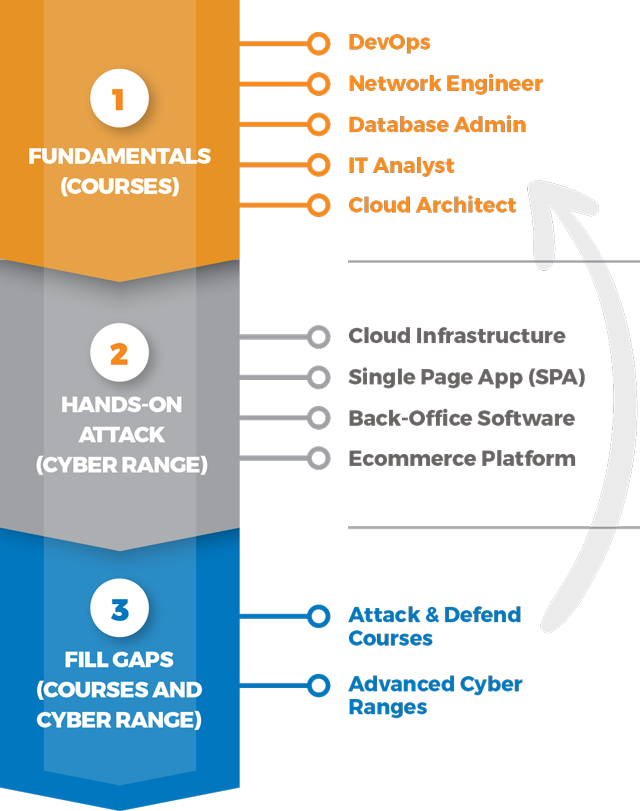
3-Step Approach to Specialized Skills
Most organizations start with fundamentals courses, followed by hands-on cyber range exercises. Detailed reporting provides targeted training recommendations, which may be taking specialized courses, moving on to an advanced range, or building a new skill.
|
Learn Fundamentals (Courses)
First, master the building blocks of secure operations: application, IT, and data security principles. |
|
Practice in Familiar Environment (Cyber Range)
See if teams can apply newly attained knowledge in our cyber ranges that span API heavy web sites, transactional systems and infrastructure. |
|
Measure & Optimize
See if teams can apply newly attained knowledge in our cyber ranges that span API heavy web sites, transactional systems and infrastructure. |
Cyber Range Reports
Get clarity on the next steps
Group reports measure staff risk over time. Individual reports isolate skill gaps and put learners on the fast track to success with specific course recommendations. Results are mapped to OWASP and the MITRE ATT&CK Framework so staff can see how hackers penetrate systems similar to theirs.
