Get Real With The CMD+CTRL Cyber Range
Unrivaled in authenticity, the CMD+CTRL Cyber Range takes engagement to a new level. Designed to give teams insight into how connected software functions and fails with respect to security. If teams can’t sniff out insecure practices, they’re likely making the same mistakes – and putting you at risk.

What is a Cyber Range?
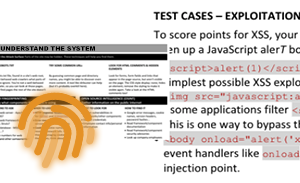
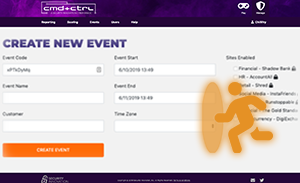
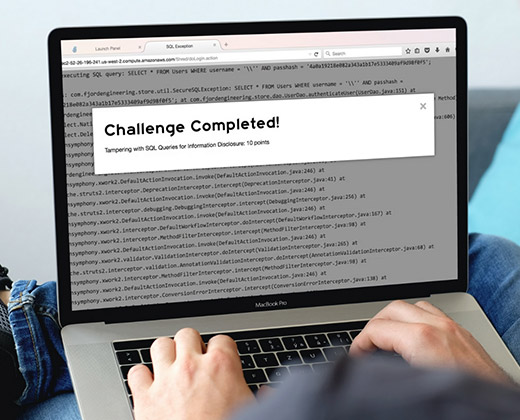
The CMD+CTRL Cyber Range is a hands-on training platform that uses insecure software environments to hone security skills. It reflects the complexity and risk of today’s tech stacks: flawed design, defenseless code, and misconfigured deployments – and tempts players to exploit them.
Who is a Cyber Range for
CMD+CTRL helps all stakeholders in the SDLC experience first-hand the impact of poor design, coding, and configuration.
The CMD+CTRL Difference
Unrivaled in authenticity, CMD+CTRL takes engagement to a whole new level. It is not designed to turn teams into hackers but to gain insight into how connected software functions and fails with respect to security. If teams can’t sniff out insecure practices, they’re likely making the same mistakes – and putting you at risk.