Base Camp Skills Development Platform
-
Role-Based Training
-
Progressive Learner Journeys
-
Skills Assessment
-
Benchmarking, Reporting & Analytics
Build Skills That Stick.
Level-up secure development skills and reduce software security risks with interactive courses and engaging exercises tailored to all roles and skill levels across the SDLC.
Minimize Rework and Maximize Productivity
A successful training program empowers teams to address vulnerabilities early in the development cycle, implement scalable security best practices and develop security champions.
250+ Courses
All roles and skill levels across the SDLC
125+ Labs
Practical, guided scenarios
11 Cyber Ranges
Ultra realistic simulated environments
What Our Clients Say
Verified reviews from industry-leading cybersecurity professionals.
Secure Software Training
The Base Camp platform combines micro-modules, labs, and real cyber range environments to build skills that stick. The result? Unrivaled engagement and measurable results to empower a security culture.

Role-Based
Keep off-the-bench time to a minimum with turnkey paths for all key roles & technologies tailored to learner goals.

Realistic Simulations
On-the job scenarios, real technology & IDE integrations build contextual skills with hands-on training.

Detailed Insights
Track progress against KPIs with baselining, assessments and automated reports.
Languages, Frameworks, Standards and more
Languages









Platforms





Frameworks





Types
-

DevSecOps
-

Infrastructure
-

Testing
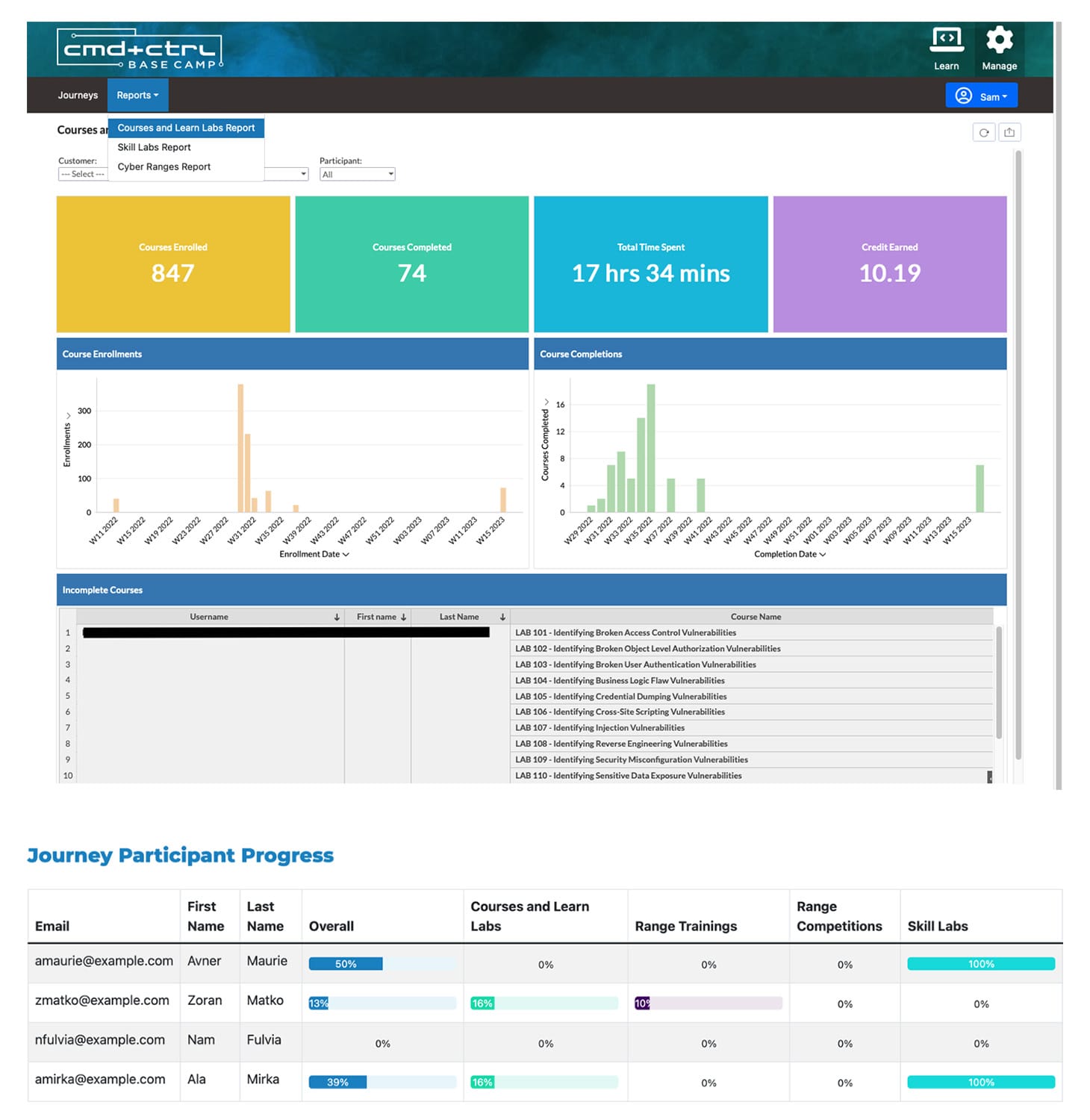
Analytics & Reporting
Robust and flexible analytics and reporting tools.
-
Deliver Executive-Level Summaries
-
Demonstrate Compliance
-
Track Learner Progress
-
Motivate Underperformers
Standards & Compliance
Maintain compliance with regulations and industry standards throughout your software development process.
OWASP | PCI | NIST | GDPR | NICE | ISO | CWE | MITRE ATT&CK | MICROSOFT SDL
Transform Your Security Posture
Software development has rapidly evolved in the wake of third-party components, cloud computing, agile methodologies and the rise of DevOps.
Software security stakeholders now include Architects, Engineers, DevOps, Analysts and more.
Up-level your software security with more secure, resilient code. Whether you are empowering a security culture, prioritizing secure coding, deploying in the cloud or complying with regulations and industry standards we’ve got you covered.