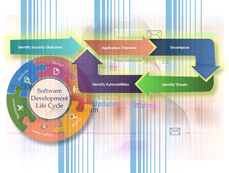
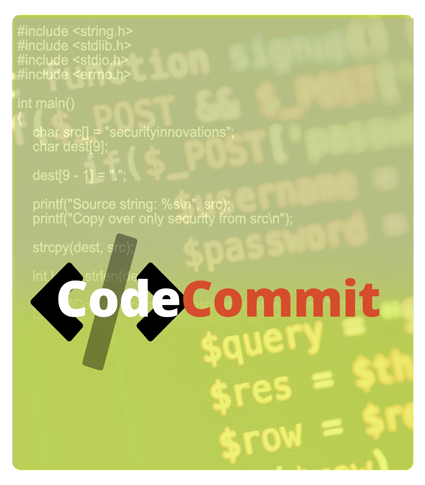
Try It – Experience the Power
of our Content & Interactivity
The best way to experience our expert and engaging approaches is to take them for a test drive.
Purpose-Built to Change Behavior
Based on proven methodologies, our interactive elements are designed to allow learners to:
- Experience the results and consequences of their choices in a safe environment
- Solidify contextual relationships by being shown (not told) what to do
- Feel like they are in control of the learning experience
Ready for a test drive? Click below!
Let's take the next step.